Strongswan can be considered as a standard ipsec service for linux.
Details for the ipsec scenario/design and strongswan can be found here
acx1100 ipsec common and policy configuration and more details can be found here
acx1100 ipsec tunnel to Strongswan
# create service interface unit for ipsec - neo4
set interfaces si-0/0/0 unit 1 description ipsec-neo4-in
set interfaces si-0/0/0 unit 1 family inet
set interfaces si-0/0/0 unit 1 service-domain inside
set interfaces si-0/0/0 unit 2 description ipsec-neo4-out
set interfaces si-0/0/0 unit 2 family inet
set interfaces si-0/0/0 unit 2 service-domain outside
# create ipsec service-set for neo4
set services service-set ipsec next-hop-service inside-service-interface si-0/0/0.1
set services service-set ipsec next-hop-service outside-service-interface si-0/0/0.2
set services service-set ipsec ipsec-vpn-options local-gateway 172.20.13.1
set services service-set ipsec ipsec-vpn-options no-anti-replay
set services service-set ipsec ipsec-vpn-rules neo4
# create ipsec service rules for neo4
set services ipsec-vpn rule neo4 term 1 from destination-address 192.168.168.0/24
set services ipsec-vpn rule neo4 term 1 from ipsec-inside-interface si-0/0/0.1
set services ipsec-vpn rule neo4 term 1 then remote-gateway 172.20.13.20
set services ipsec-vpn rule neo4 term 1 then dynamic ike-policy ike-pol
set services ipsec-vpn rule neo4 term 1 then dynamic ipsec-policy ipsec-pol
set services ipsec-vpn rule neo4 match-direction input
# add static route to neo4 remote network
set routing-options static route 192.168.168.0/24 next-hop si-0/0/0.1Strongswan (NEO4) ipsec tunnel to acx1100
NEO4 podman network, container and iptables rule related to podman nat and ipsec policy.
This is only informative configuration .. details are out of scope here
# create podman network
podman network create --subnet 192.168.168.0/24 --gateway 192.168.168.254 acx
# create podman container
podman run --cgroup-manager cgroupfs --rm -it --privileged --network=acx --ip=192.168.168.10 jonlabelle/network-tools
# iptables/ipsec policy for podman network
iptables -t nat -I POSTROUTING -s 192.168.168.0/24 -m policy --dir out --pol ipsec -j ACCEPTStrongswan configuration
# We need only swanctl configuration /etc/swanctl/conf.d/acx1100.conf
# Section defining IKE connection configurations.
connections {
# Section for an IKE connection named <conn>.
acx1100 {
# IKE major version to use for connection.
version = 2
# Local address(es) to use for IKE communication, comma separated.
local_addrs = 172.20.13.20
# Remote address(es) to use for IKE communication, comma separated.
remote_addrs = 172.20.13.1
# Comma separated proposals to accept for IKE.
proposals = aes128-sha1-modp1024
# Section for a local authentication round.
local {
# Authentication to perform locally (pubkey, psk, xauth[-backend] or
# eap[-method]).
auth = psk
# IKE identity to use for authentication round.
id = "172.20.13.20"
}
# Section for a remote authentication round.
remote {
# IKE identity to expect for authentication round.
id = "172.20.13.1"
# Authentication to expect from remote (pubkey, psk, xauth[-backend]
# or eap[-method]).
auth = psk
}
children {
# CHILD_SA configuration sub-section.
local-remote {
# Local traffic selectors to include in CHILD_SA.
local_ts = 192.168.168.0/24
# Remote selectors to include in CHILD_SA.
remote_ts = 10.0.0.0/30
# ESP proposals to offer for the CHILD_SA.
esp_proposals = aes128-sha1
# IPsec Mode to establish (tunnel, transport, transport_proxy,
# beet, pass or drop).
mode = tunnel
# Action to perform after loading the configuration (none, trap,
# start).
start_action = trap
}
}
}
}
# Section defining secrets for IKE/EAP/XAuth authentication and private key
# decryption.
secrets {
# IKE preshared secret section for a specific secret.
ike-acx1100 {
# Value of the IKE preshared secret.
secret = "1q2w3e"
# IKE identity the IKE preshared secret belongs to.
id-1 = "172.20.13.20"
id-2 = "172.20.13.1"
}
}Validation
NEO4 Strongswan / podman container
# load all swanctl configurations
root@noe4:~# swanctl -q
loaded ike secret 'ike-acx1100'
no authorities found, 0 unloaded
no pools found, 0 unloaded
loaded connection 'acx1100'
successfully loaded 1 connections, 0 unloaded
# list loaded configurations
root@noe4:~# swanctl -L
acx1100: IKEv2, no reauthentication, rekeying every 14400s
local: 172.20.13.20
remote: 172.20.13.1
local pre-shared key authentication:
id: 172.20.13.20
remote pre-shared key authentication:
id: 172.20.13.1
local-remote: TUNNEL, rekeying every 3600s
local: 192.168.168.0/24
remote: 10.0.0.0/30
# list currently active IKE_SAs
root@noe4:~# swanctl -l
acx1100: #2, ESTABLISHED, IKEv2, 1189ce124b8a97e0_i 423b1372332901df_r*
local '172.20.13.20' @ 172.20.13.20[500]
remote '172.20.13.1' @ 172.20.13.1[500]
AES_CBC-128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
established 15s ago, rekeying in 14020s
local-remote: #2, reqid 1, INSTALLED, TUNNEL, ESP:AES_CBC-128/HMAC_SHA1_96
installed 15s ago, rekeying in 3355s, expires in 3945s
in cdc5ca79, 0 bytes, 0 packets
out 7d7c7703, 0 bytes, 0 packets
local 192.168.168.0/24
remote 10.0.0.0/30
# podman container ping acx1100 LRC
[network-tools]$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 5a:e1:77:e7:2f:29 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 192.168.168.10/24 brd 192.168.168.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::58e1:77ff:fee7:2f29/64 scope link
valid_lft forever preferred_lft forever
[network-tools]$ ping -c 3 10.0.0.2
PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data.
64 bytes from 10.0.0.2: icmp_seq=1 ttl=62 time=1.36 ms
64 bytes from 10.0.0.2: icmp_seq=2 ttl=62 time=1.38 ms
64 bytes from 10.0.0.2: icmp_seq=3 ttl=62 time=1.45 ms
--- 10.0.0.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2004ms
rtt min/avg/max/mdev = 1.357/1.396/1.450/0.039 msacx1100 / LRC
# check acx1100 ike sa
root@acx1100> show services ipsec-vpn ike security-associations 172.20.13.20 brief
Remote Address State Initiator cookie Responder cookie Exchange type
172.20.13.20 Matured 1189ce124b8a97e0 423b1372332901df IKEv2
root@acx1100> show services ipsec-vpn ike security-associations 172.20.13.20 detail
IKE peer 172.20.13.20
Role: Initiator, State: Matured
Initiator cookie: 1189ce124b8a97e0, Responder cookie: 423b1372332901df
Exchange type: IKEv2, Authentication method: Pre-shared-keys
Local: 172.20.13.1, Remote: 172.20.13.20
Lifetime: Expires in 3101 seconds
Peer ike-id: ipv4(any:0,[0..3]=172.20.13.20)
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes128-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : 2
Traffic statistics:
Input bytes : 524
Output bytes : 524
Input packets: 2
Output packets: 2
Flags: IKE SA created
IPSec security associations: 2 created, 0 deleted
# check acx1100 ipsec sa
root@acx1100> show services ipsec-vpn ipsec security-associations ipsec detail
Service set: ipsec, IKE Routing-instance: default
Rule: neo4, Term: 1, Tunnel index: 1
Local gateway: 172.20.13.1, Remote gateway: 172.20.13.20
IPSec inside interface: si-0/0/0.1, Tunnel MTU: 1500
UDP encapsulate: Disabled, UDP Destination port: 0
Local identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote identity: ipv4_subnet(any:0,[0..7]=192.168.168.0/24)
NATT Detection: Not Detected, NATT keepalive interval: 0
Total uptime: 0 days 0 hrs 9 mins 31 secs
Direction: inbound, SPI: 2105308931, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (128 bits)
Soft lifetime: Expires in 26830 seconds
Hard lifetime: Expires in 28229 seconds
Anti-replay service: Disabled
Copy ToS: Disabled, ToS value: 0
Copy TTL: Disabled, TTL value: 64
SA lifetime: 28800 seconds
Direction: outbound, SPI: 3452291705, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (128 bits)
Soft lifetime: Expires in 26830 seconds
Hard lifetime: Expires in 28229 seconds
Anti-replay service: Disabled
Copy ToS: Disabled, ToS value: 0
Copy TTL: Disabled, TTL value: 64
SA lifetime: 28800 seconds
# LRC ping NEO4 podman container
lrc@acx1100:lrc> show interfaces terse | match ge-0/1/1
ge-0/1/1
ge-0/1/1.0 up up inet 10.0.0.2/30
lrc@acx1100:lrc> ping count 3 192.168.168.10
PING 192.168.168.10 (192.168.168.10): 56 data bytes
64 bytes from 192.168.168.10: icmp_seq=0 ttl=62 time=1.811 ms
64 bytes from 192.168.168.10: icmp_seq=1 ttl=62 time=1.771 ms
64 bytes from 192.168.168.10: icmp_seq=2 ttl=62 time=1.687 ms
--- 192.168.168.10 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max/stddev = 1.687/1.756/1.811/0.052 msWireshark - network switch between acx1100 and NEO4
NEO4(podman container) to acx1100(LRC)
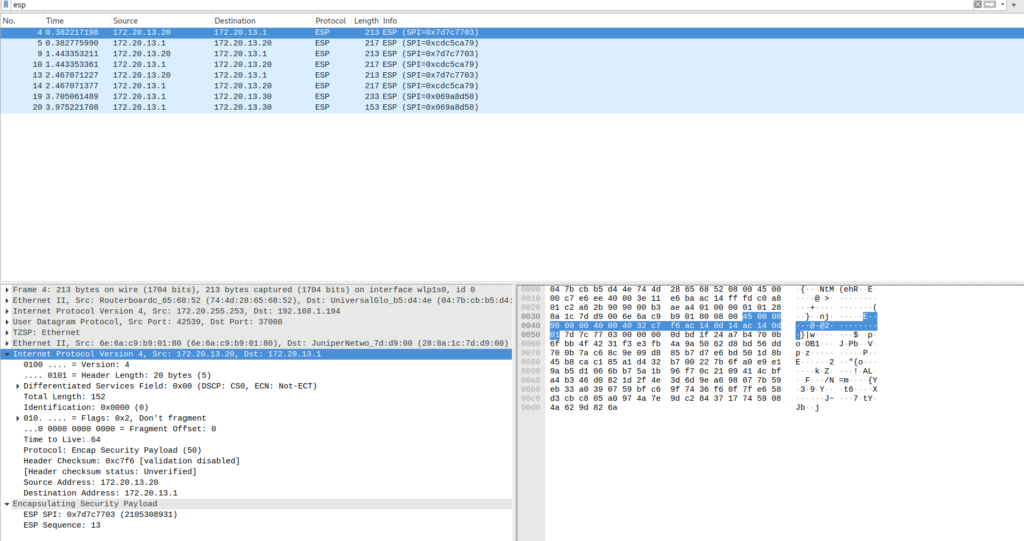
acx1100(LRC) to NEO4(podman container)
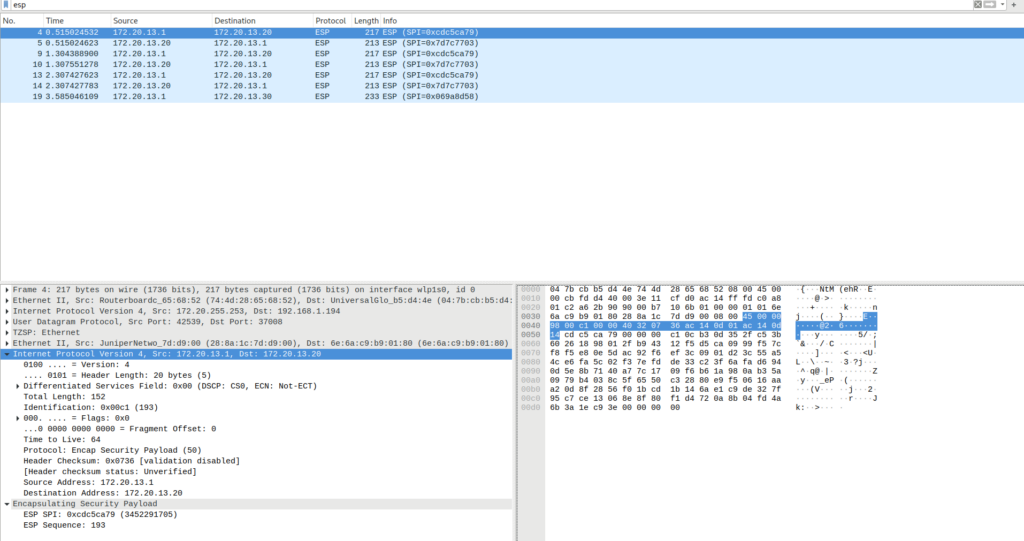
Final check .. we should NOT see any not encrypted icmp
