Mikrotik provide amazing affordable hardware and RouterOS software. RouterOS have bazillion number of functionalities however IPSEC VTI is missing (*2023), so only solution is to use IPIP or GRE tunnel and encrypt them with IPSEC, if for example dynamic routing is required between 2 remote sites.
Mikrotik Cloud Hosted Router (CHR) (ROS v7) is a GNS3 node, we will encrypt gre tunnel endpoints to acx1100 also will exchange routes with OSPF.
acx1100 will encrypt gre tunnels endpoints, tunnel interface (gr-) is attached to logical system LRC, LRC will exchange routes via OSPF with Mikrotik CHR
Details for the ipsec scenario/design and strongswan can be found here
acx1100 ipsec common and policy configuration and more details can be found here
Mikrotik CHR configuration
some of the configuration like dhcp-server to lan networks and others are out of the scope
# 2023-12 RouterOS 7.13
# we will create tow bridges, in ROS bridges are used as virtual interfaces .. loopback interface as well
/interface bridge
add name=loopback protocol-mode=none
# this interface will be used as GRE endpoint
add name=tunnel-acx protocol-mode=none
# create GRE tunnel to acx1100
/interface gre
add allow-fast-path=no local-address=10.10.10.10 name=gre-tunnel-acx remote-address=10.0.0.2
# ip address configuration
# ether1 - wan
# ether2 - lan network to pc1(gns3 vpc node)
# ether3 - lan network to pc2(gns3 vpc node)
# tunnel-acx - (bridge) used for gre tunnel endpoint
# gre-tunnel-acx - gre tunnel ip address
# loopback (bridge) ip address
/ip address
add address=172.20.13.30/24 interface=ether1 network=172.20.13.0
add address=192.168.30.254/24 interface=ether2 network=192.168.30.0
add address=192.168.31.254/24 interface=ether3 network=192.168.31.0
add address=10.10.10.10 interface=tunnel-acx network=10.10.10.10
add address=10.1.1.2/30 interface=gre-tunnel-acx network=10.1.1.0
add address=200.0.0.1 interface=loopback network=200.0.0.1
# ipsec configuration
/ip ipsec profile
add dh-group=modp1024 enc-algorithm=aes-128 name=profile-acx nat-traversal=no
/ip ipsec peer
add address=172.20.13.1/32 exchange-mode=ike2 local-address=172.20.13.30 name=peer-acx profile=profile-acx
/ip ipsec proposal
add enc-algorithms=aes-128-cbc name=proposal-acx
/ip ipsec identity
add peer=peer-acx
# we will encrypt gre tunnel endpoints (local tunnel-acx (bridge) ) and acx1100 network to LRC
/ip ipsec policy
set 0 disabled=yes
add dst-address=10.0.0.0/30 level=unique peer=peer-acx proposal=proposal-acx src-address=10.10.10.10/32 tunnel=yes
# we will use gre tunnel interface (gre-tunnel-acx) for OSPF
/routing ospf instance
add disabled=no name=ospf-instance-acx
/routing ospf area
add disabled=no instance=ospf-instance-acx name=ospf-area-acx
/routing ospf interface-template
add area=ospf-area-acx disabled=no interfaces=gre-tunnel-acx type=ptp
add area=ospf-area-acx disabled=no interfaces=ether2 passive
add area=ospf-area-acx disabled=no interfaces=ether3 passive
add area=ospf-area-acx disabled=no interfaces=loopback passiveacx1100 configuration
# create service interface unit for ipsec - mikrotik
set interfaces si-0/0/0 unit 3 description ipsec-mikrotik-in
set interfaces si-0/0/0 unit 3 family inet
set interfaces si-0/0/0 unit 3 service-domain inside
set interfaces si-0/0/0 unit 4 description ipsec-mikrotik-out
set interfaces si-0/0/0 unit 4 family inet
set interfaces si-0/0/0 unit 4 service-domain outside
# create ipsec service-set for mikrotik
set services service-set ipsec-mk next-hop-service inside-service-interface si-0/0/0.3
set services service-set ipsec-mk next-hop-service outside-service-interface si-0/0/0.4
set services service-set ipsec-mk ipsec-vpn-options local-gateway 172.20.13.1
set services service-set ipsec-mk ipsec-vpn-options no-anti-replay
set services service-set ipsec-mk ipsec-vpn-rules mikrotik
# create ipsec service rules for mikrotik
set services ipsec-vpn rule mikrotik term 1 from destination-address 10.10.10.10/32
set services ipsec-vpn rule mikrotik term 1 from ipsec-inside-interface si-0/0/0.3
set services ipsec-vpn rule mikrotik term 1 then remote-gateway 172.20.13.30
set services ipsec-vpn rule mikrotik term 1 then dynamic ike-policy ike-pol
set services ipsec-vpn rule mikrotik term 1 then dynamic ipsec-policy ipsec-pol
set services ipsec-vpn rule mikrotik match-direction input
# add route to mikrotik remote gre endpoint via si-0/0/0.3 << inline-service interface (ipsec-inside-interface)
set routing-options static route 10.10.10.10/32 next-hop si-0/0/0.3
# add gre interface (ge-0/0/0.0) to LRC
set logical-systems lrc interfaces gr-0/0/0 unit 0Logical systems configuration
# --- LRC
# set default route to acx1100
set routing-options static route 0.0.0.0/0 next-hop 10.0.0.1
# create gre tunnel to mikrotik
set interfaces gr-0/0/0 unit 0 tunnel source 10.0.0.2
set interfaces gr-0/0/0 unit 0 tunnel destination 10.10.10.10
set interfaces gr-0/0/0 unit 0 family inet address 10.1.1.1/30
# OSPF via gre tunnel interface (gr-0/0/0.0) and interfaces connected to all other logical systems
set protocols ospf area 0 interface gr-0/0/0.0
set protocols ospf area 0 interface ge-0/0/5.0
set protocols ospf area 0 interface ge-0/0/6.0
set protocols ospf area 0 interface ge-0/0/7.0
set protocols ospf area 0 interface lo0.123 passive
# --- LR1 (ospf)
set protocols ospf area 0 interface ge-0/0/1.0
set protocols ospf area 0 interface lo0.1 passive
# --- LR2 (ospf)
set protocols ospf area 0 interface ge-0/0/2.0
set protocols ospf area 0 interface lo0.2 passive
# --- LR3 (ospf)
set protocols ospf area 0 interface ge-0/0/3.0
set protocols ospf area 0 interface lo0.3 passive
Validation
Mikrotik CHR
# check ipsec peers
[admin@mikrotik] > /ip/ipsec/active-peers/print
Columns: ID, STATE, UPTIME, PH2-TOTAL, REMOTE-ADDRESS
# ID STATE UPTIME PH2-TOTAL REMOTE-ADDRESS
0 172.20.13.1 established 12m38s 1 172.20.13.1
# check ipsec SA
[admin@mikrotik] > /ip/ipsec/installed-sa/print
Flags: S - SEEN-TRAFFIC; E - ESP
Columns: SPI, STATE, SRC-ADDRESS, DST-ADDRESS, AUTH-ALGORITHM, ENC-ALGORITHM, ENC-KEY-SIZE
# SPI STATE SRC-ADDRESS DST-ADDRESS AUTH-ALGORITHM ENC-ALGORITHM ENC-KEY-SIZE
0 SE 0xE20EABD mature 172.20.13.1 172.20.13.30 sha1 aes-cbc 128
1 SE 0x5273EFAA mature 172.20.13.30 172.20.13.1 sha1 aes-cbc 128
# check interfaces ( number 8 is gre tunnel to acx1100)
[admin@mikrotik] > /interface/print brief
Flags: R - RUNNING
Columns: NAME, TYPE, ACTUAL-MTU, L2MTU, MAC-ADDRESS
# NAME TYPE ACTUAL-MTU L2MTU MAC-ADDRESS
0 R ether1 ether 1500 0C:52:D3:A3:00:00
1 R ether2 ether 1500 0C:52:D3:A3:00:01
2 R ether3 ether 1500 0C:52:D3:A3:00:02
3 ether4 ether 1500 0C:52:D3:A3:00:03
4 ether5 ether 1500 0C:52:D3:A3:00:04
5 ether6 ether 1500 0C:52:D3:A3:00:05
6 ether7 ether 1500 0C:52:D3:A3:00:06
7 ether8 ether 1500 0C:52:D3:A3:00:07
8 R gre-tunnel-acx gre-tunnel 1414 65535
9 R loopback bridge 1500 65535 CA:0A:4F:6D:56:01
10 R tunnel-acx bridge 1500 65535 1A:7B:0E:FC:8D:EB
# check ospf neighbors
[admin@mikrotik] > /routing/ospf/neighbor/print
Flags: V - virtual; D - dynamic
0 D instance=ospf-instance-acx area=ospf-area-acx address=10.1.1.1 router-id=100.1.2.3 state="Full" state-changes=10 adjacency=1d2h55m18s timeout=40s
# check mikrotik routing tables
[admin@mikrotik] > /ip/route/print
Flags: D - DYNAMIC; A - ACTIVE; c - CONNECT, s - STATIC, o - OSPF
Columns: DST-ADDRESS, GATEWAY, DISTANCE
# DST-ADDRESS GATEWAY DISTANCE
0 As 0.0.0.0/0 172.20.13.254 1
DAo 10.0.1.0/30 10.1.1.1%gre-tunnel-acx 110
DAo 10.0.2.0/30 10.1.1.1%gre-tunnel-acx 110
DAo 10.0.3.0/30 10.1.1.1%gre-tunnel-acx 110
DAc 10.1.1.0/30 gre-tunnel-acx 0
DAc 10.10.10.10/32 tunnel-acx 0
DAo 100.1.1.1/32 10.1.1.1%gre-tunnel-acx 110
DAo 100.1.2.3/32 10.1.1.1%gre-tunnel-acx 110
DAo 100.2.2.2/32 10.1.1.1%gre-tunnel-acx 110
DAo 100.3.3.3/32 10.1.1.1%gre-tunnel-acx 110
DAc 172.20.13.0/24 ether1 0
DAc 192.168.30.0/24 ether2 0
DAc 192.168.31.0/24 ether3 0
DAc 200.0.0.1/32 loopback 0
# ping LRC loopback
[admin@mikrotik] > ping count=3 100.1.2.3
SEQ HOST SIZE TTL TIME STATUS
0 100.1.2.3 56 64 1ms807us
1 100.1.2.3 56 64 1ms779us
2 100.1.2.3 56 64 1ms646us
sent=3 received=3 packet-loss=0% min-rtt=1ms646us avg-rtt=1ms744us max-rtt=1ms807us
# ping LR1,LR2,LR3 loopback >> The result is NOT AWESOME !!!
[admin@mikrotik] > ping count=3 100.1.1.1
SEQ HOST SIZE TTL TIME STATUS
0 100.1.1.1 timeout
1 100.1.1.1 timeout
2 100.1.1.1 timeout
sent=3 received=0 packet-loss=100%
[admin@mikrotik] > ping count=3 100.2.2.2
SEQ HOST SIZE TTL TIME STATUS
0 100.2.2.2 timeout
1 100.2.2.2 timeout
2 100.2.2.2 timeout
sent=3 received=0 packet-loss=100%
[admin@mikrotik] > ping count=3 100.3.3.3
SEQ HOST SIZE TTL TIME STATUS
0 100.3.3.3 timeout
1 100.3.3.3 timeout
2 100.3.3.3 timeout
sent=3 received=0 packet-loss=100%PC1,PC2
# ping LRC loopback (PC1)
PC1> ping 100.1.2.3
84 bytes from 100.1.2.3 icmp_seq=1 ttl=63 time=8.511 ms
84 bytes from 100.1.2.3 icmp_seq=2 ttl=63 time=9.520 ms
84 bytes from 100.1.2.3 icmp_seq=3 ttl=63 time=9.776 ms
84 bytes from 100.1.2.3 icmp_seq=4 ttl=63 time=8.826 ms
84 bytes from 100.1.2.3 icmp_seq=5 ttl=63 time=9.007 ms
# ping LR1,LR2,LR3 loopback (PC1) >> The result is NOT AWESOME !!!
PC1> ping 100.1.1.1
100.1.1.1 icmp_seq=1 timeout
100.1.1.1 icmp_seq=2 timeout
100.1.1.1 icmp_seq=3 timeout
100.1.1.1 icmp_seq=4 timeout
100.1.1.1 icmp_seq=5 timeout
PC1> ping 100.2.2.2
100.2.2.2 icmp_seq=1 timeout
100.2.2.2 icmp_seq=2 timeout
100.2.2.2 icmp_seq=3 timeout
100.2.2.2 icmp_seq=4 timeout
100.2.2.2 icmp_seq=5 timeout
PC1> ping 100.3.3.3
100.3.3.3 icmp_seq=1 timeout
100.3.3.3 icmp_seq=2 timeout
100.3.3.3 icmp_seq=3 timeout
100.3.3.3 icmp_seq=4 timeout
100.3.3.3 icmp_seq=5 timeout
# ping LRC loopback (PC2)
PC2> ping 100.1.2.3
84 bytes from 100.1.2.3 icmp_seq=1 ttl=63 time=1.997 ms
84 bytes from 100.1.2.3 icmp_seq=2 ttl=63 time=1.875 ms
84 bytes from 100.1.2.3 icmp_seq=3 ttl=63 time=2.009 ms
84 bytes from 100.1.2.3 icmp_seq=4 ttl=63 time=2.341 ms
84 bytes from 100.1.2.3 icmp_seq=5 ttl=63 time=5.358 ms
# ping LR1,LR2,LR3 loopback (PC2) >> The result is NOT AWESOME !!!
PC2> ping 100.1.1.1
100.1.1.1 icmp_seq=1 timeout
100.1.1.1 icmp_seq=2 timeout
100.1.1.1 icmp_seq=3 timeout
100.1.1.1 icmp_seq=4 timeout
100.1.1.1 icmp_seq=5 timeout
PC2> ping 100.2.2.2
100.2.2.2 icmp_seq=1 timeout
100.2.2.2 icmp_seq=2 timeout
100.2.2.2 icmp_seq=3 timeout
100.2.2.2 icmp_seq=4 timeout
100.2.2.2 icmp_seq=5 timeout
PC2> ping 100.3.3.3
100.3.3.3 icmp_seq=1 timeout
100.3.3.3 icmp_seq=2 timeout
100.3.3.3 icmp_seq=3 timeout
100.3.3.3 icmp_seq=4 timeout
100.3.3.3 icmp_seq=5 timeout
acx1100
# check acx1100 ike sa
root@acx1100> show services ipsec-vpn ike security-associations 172.20.13.30 detail
IKE peer 172.20.13.30
Role: Responder, State: Matured
Initiator cookie: e05c694ce4dd8bfd, Responder cookie: 55bf7dcf8c6128c3
Exchange type: IKEv2, Authentication method: Pre-shared-keys
Local: 172.20.13.1, Remote: 172.20.13.30
Lifetime: Expires in 2302 seconds
Peer ike-id: ipv4(any:0,[0..3]=172.20.13.30)
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes128-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : 2
Traffic statistics:
Input bytes : 1868
Output bytes : 1260
Input packets: 12
Output packets: 12
Flags: IKE SA created
IPSec security associations: 2 created, 0 deleted
# check acx1100 ipsec sa
root@acx1100> show services ipsec-vpn ipsec security-associations ipsec-mk detail
Service set: ipsec-mk, IKE Routing-instance: default
Rule: mikrotik, Term: 1, Tunnel index: 3
Local gateway: 172.20.13.1, Remote gateway: 172.20.13.30
IPSec inside interface: si-0/0/0.3, Tunnel MTU: 1500
UDP encapsulate: Disabled, UDP Destination port: 0
Local identity: ipv4_subnet(any:0,[0..7]=10.0.0.0/30)
Remote identity: ipv4(any:0,[0..3]=10.10.10.10)
NATT Detection: Not Detected, NATT keepalive interval: 0
Total uptime: 0 days 0 hrs 21 mins 39 secs
Direction: inbound, SPI: 117500600, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (128 bits)
Soft lifetime: Expires in 26057 seconds
Hard lifetime: Expires in 27501 seconds
Anti-replay service: Disabled
Copy ToS: Disabled, ToS value: 0
Copy TTL: Disabled, TTL value: 64
SA lifetime: 28800 seconds
Direction: outbound, SPI: 52058299, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (128 bits)
Soft lifetime: Expires in 26057 seconds
Hard lifetime: Expires in 27501 seconds
Anti-replay service: Disabled
Copy ToS: Disabled, ToS value: 0
Copy TTL: Disabled, TTL value: 64
SA lifetime: 28800 seconds
LRC
# check gre tunnel interface
lrc@acx1100:lrc> show interfaces gr-0/0/0.0 brief
Logical interface gr-0/0/0.0
Flags: Up Point-To-Point SNMP-Traps 0x0 IP-Header 10.10.10.10:10.0.0.2:47:df:64:00000000000b000b Encapsulation: GRE-NULL
Gre keepalives configured: Off, Gre keepalives adjacency state: down
inet 10.1.1.1/30
# check ospf neighbors
lrc@acx1100:lrc> show ospf neighbor
Address Interface State ID Pri Dead
10.0.1.1 ge-0/0/5.0 Full 100.1.1.1 128 33
10.0.2.1 ge-0/0/6.0 Full 100.2.2.2 128 34
10.0.3.1 ge-0/0/7.0 Full 100.3.3.3 128 36
10.1.1.2 gr-0/0/0.0 Full 200.0.0.1 128 32
# check LRC routing tables
lrc@acx1100:lrc> show route protocol ospf
inet.0: 19 destinations, 20 routes (19 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
10.1.1.0/30 [OSPF/10] 4d 00:02:13, metric 1
> via gr-0/0/0.0
100.1.1.1/32 *[OSPF/10] 3d 14:59:05, metric 1
> to 10.0.1.1 via ge-0/0/5.0
100.2.2.2/32 *[OSPF/10] 3d 14:57:57, metric 1
> to 10.0.2.1 via ge-0/0/6.0
100.3.3.3/32 *[OSPF/10] 3d 14:57:41, metric 1
> to 10.0.3.1 via ge-0/0/7.0
192.168.30.0/24 *[OSPF/10] 1d 03:38:44, metric 2
> via gr-0/0/0.0
192.168.31.0/24 *[OSPF/10] 1d 03:38:44, metric 2
> via gr-0/0/0.0
200.0.0.1/32 *[OSPF/10] 1d 03:38:44, metric 2
> via gr-0/0/0.0
224.0.0.5/32 *[OSPF/10] 4d 00:02:18, metric 1
MultiRecv
inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
# check ping to mikrotik chr loopback
lrc@acx1100:lrc> ping count 3 200.0.0.1
PING 200.0.0.1 (200.0.0.1): 56 data bytes
64 bytes from 200.0.0.1: icmp_seq=0 ttl=64 time=2.117 ms
64 bytes from 200.0.0.1: icmp_seq=1 ttl=64 time=1.853 ms
64 bytes from 200.0.0.1: icmp_seq=2 ttl=64 time=1.757 ms
--- 200.0.0.1 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max/stddev = 1.757/1.909/2.117/0.152 ms
# check ping to PC1
lrc@acx1100:lrc> ping count 3 192.168.30.253
PING 192.168.30.253 (192.168.30.253): 56 data bytes
64 bytes from 192.168.30.253: icmp_seq=0 ttl=63 time=2.064 ms
64 bytes from 192.168.30.253: icmp_seq=1 ttl=63 time=2.374 ms
64 bytes from 192.168.30.253: icmp_seq=2 ttl=63 time=2.099 ms
--- 192.168.30.253 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max/stddev = 2.064/2.179/2.374/0.139 ms
# check ping to PC2
lrc@acx1100:lrc> ping count 3 192.168.31.253
PING 192.168.31.253 (192.168.31.253): 56 data bytes
64 bytes from 192.168.31.253: icmp_seq=0 ttl=63 time=3.283 ms
64 bytes from 192.168.31.253: icmp_seq=1 ttl=63 time=2.334 ms
64 bytes from 192.168.31.253: icmp_seq=2 ttl=63 time=2.236 ms
--- 192.168.31.253 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max/stddev = 2.236/2.618/3.283/0.472 ms
LR1,LR2,LR3
We have same config for LR1,LR2 and LR3 .. will validate only LR1
# check ospf neighbors
lr1@acx1100:lr1> show ospf neighbor
Address Interface State ID Pri Dead
10.0.1.2 ge-0/0/1.0 Full 100.1.2.3 128 39
# check LRC routing tables
lr1@acx1100:lr1> show route protocol ospf
inet.0: 13 destinations, 13 routes (13 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
10.0.2.0/30 *[OSPF/10] 3d 15:04:50, metric 2
> to 10.0.1.2 via ge-0/0/1.0
10.0.3.0/30 *[OSPF/10] 3d 15:04:50, metric 2
> to 10.0.1.2 via ge-0/0/1.0
10.1.1.0/30 *[OSPF/10] 3d 15:04:50, metric 2
> to 10.0.1.2 via ge-0/0/1.0
100.1.2.3/32 *[OSPF/10] 3d 15:04:50, metric 1
> to 10.0.1.2 via ge-0/0/1.0
100.2.2.2/32 *[OSPF/10] 3d 15:03:45, metric 2
> to 10.0.1.2 via ge-0/0/1.0
100.3.3.3/32 *[OSPF/10] 3d 15:03:29, metric 2
> to 10.0.1.2 via ge-0/0/1.0
192.168.30.0/24 *[OSPF/10] 1d 03:44:32, metric 3
> to 10.0.1.2 via ge-0/0/1.0
192.168.31.0/24 *[OSPF/10] 1d 03:44:32, metric 3
> to 10.0.1.2 via ge-0/0/1.0
200.0.0.1/32 *[OSPF/10] 1d 03:44:32, metric 3
> to 10.0.1.2 via ge-0/0/1.0
224.0.0.5/32 *[OSPF/10] 3d 15:05:00, metric 1
MultiRecv
inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
# check ping to LRC loopback
lr1@acx1100:lr1> ping count 3 100.1.2.3
PING 100.1.2.3 (100.1.2.3): 56 data bytes
64 bytes from 100.1.2.3: icmp_seq=0 ttl=64 time=1.050 ms
64 bytes from 100.1.2.3: icmp_seq=1 ttl=64 time=0.967 ms
64 bytes from 100.1.2.3: icmp_seq=2 ttl=64 time=1.034 ms
--- 100.1.2.3 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max/stddev = 0.967/1.017/1.050/0.036 ms
# check ping to mikrotik chr loopback >> The result is NOT AWESOME !!!
lr1@acx1100:lr1> ping count 3 200.0.0.1
PING 200.0.0.1 (200.0.0.1): 56 data bytes
--- 200.0.0.1 ping statistics ---
3 packets transmitted, 0 packets received, 100% packet loss
# check ping to PC1 >> The result is NOT AWESOME !!!
lr1@acx1100:lr1> ping count 3 192.168.30.253
PING 192.168.30.253 (192.168.30.253): 56 data bytes
--- 192.168.30.253 ping statistics ---
3 packets transmitted, 0 packets received, 100% packet loss
# check ping to PC2 >> The result is NOT AWESOME !!!
lr1@acx1100:lr1> ping count 3 192.168.31.253
PING 192.168.31.253 (192.168.31.253): 56 data bytes
--- 192.168.31.253 ping statistics ---
3 packets transmitted, 0 packets received, 100% packet loss
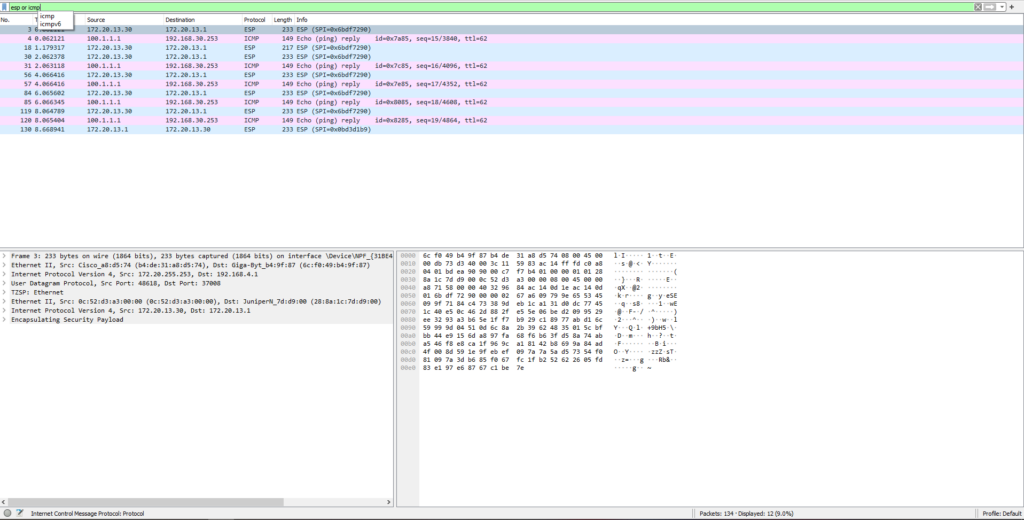
Wireshark – network switch between acx1100 and Mikrotik CHR
PC1 to acx1100(LRC)
We can see everything is encrypted with ipsec/esp
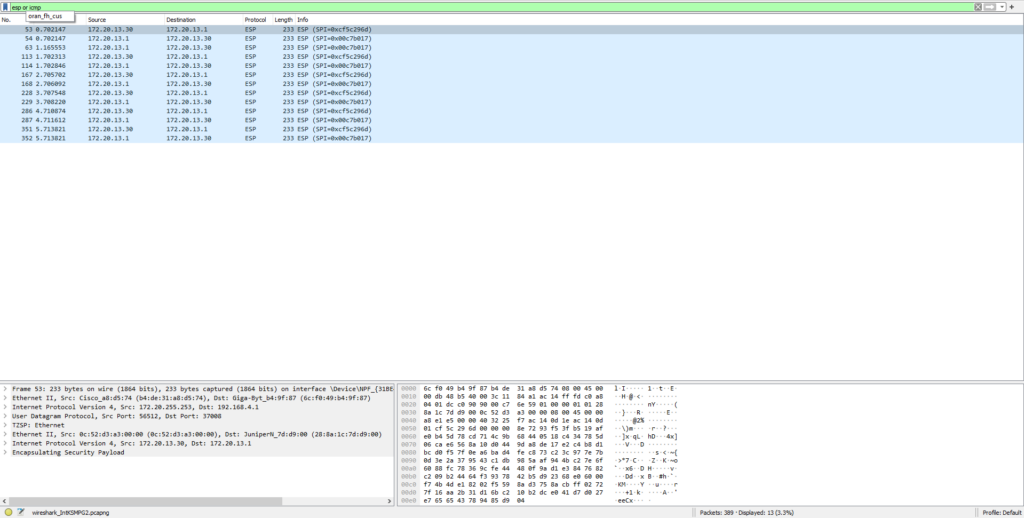
PC1 to acx1100(LR1)
We can see NOT encrypted ICMP echo reply from LR1 to PC1, however everything else is ipsec/esp encrypted including ICMP echo send.
This explain why ping(traffic) MikrotikCHR/PC1/PC2 <> LR1/2/3 NOT working !!!