IPSEC
acx1100 uses inline-service for IPsec (tunnel mode) which is limited only for inbound encryption; however, we still can be happy with the functionality (but not in all cases).
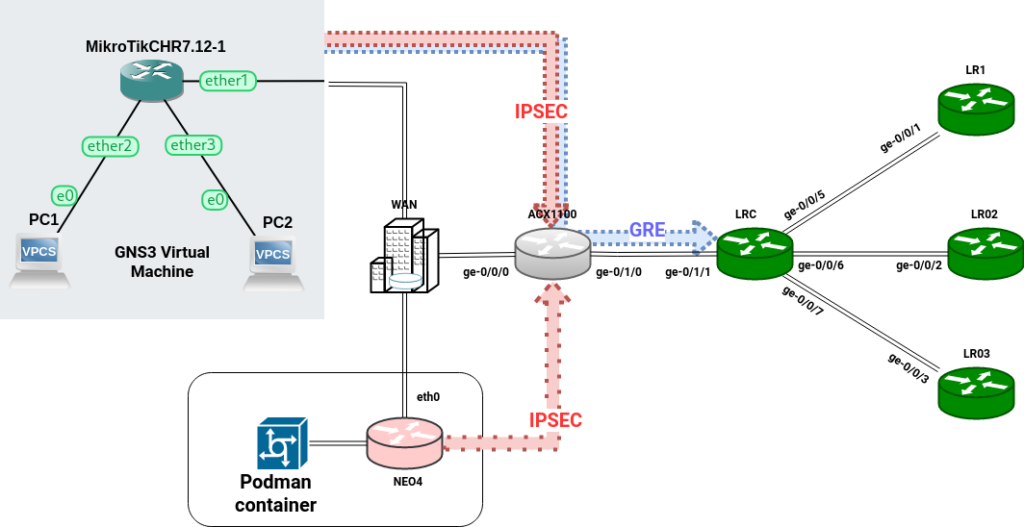
We will reuse our Lab Design (except FRR) and Logical Systems configuration as base configuration.
All remote IPsec endpoints are not directly connected to the acx1100.
| Endpoint | Public IP | Local Networks (Encrypted) |
|---|---|---|
| acx1100 (LRC) | 172.20.13.1 | 10.0.0.0/30 (GRE/OSPF on all logical systems networks) |
| NEO4 | 172.20.13.20 | 192.168.168.0/24 (Podman network) |
| MikroTik (CHR) | 172.20.13.30 | 192.168.30.0/24 (PC1 network), 192.168.31.0/24 (PC2 network) |
acx1100 (IPsec inline-service)
I strongly suggest checking the following links to understand the configurations in this lab:
- Service Sets (inline-services)
- IPsec Overview
- Configuration Guidelines (Static Endpoint IPsec Tunnels)
- Configuring IPsec Rules
NEO4 (Strongswan)
NEO4 is an ARM64 Linux SBC (ex-FRR) with a Podman container.
We will create an IPsec tunnel with StrongSwan to encrypt both the Podman network and the acx1100 LRC network.
MikroTik (ROS 7)
The MikroTik router is a node in GNS3 virtual machines.
We will create a GRE tunnel between the MikroTik and the LRC and encrypt it with IPsec; the GRE tunnel will be used for OSPF.
We will also evaluate what works and what does not in this IPsec/GRE scenario!