Labs IPsec Strongswan endpoint
IPsec Strongswan endpoint
Strongswan can be considered as a standard IPsec service for Linux.
Details for the IPsec scenario/design and Strongswan can be found here.
ACX1100 IPsec common and policy configuration and more details can be found here.
acx1100 ipsec tunnel to Strongswan
# create service interface unit for ipsec - neo4
set interfaces si-0/0/0 unit 1 description ipsec-neo4-in
set interfaces si-0/0/0 unit 1 family inet
set interfaces si-0/0/0 unit 1 service-domain inside
set interfaces si-0/0/0 unit 2 description ipsec-neo4-out
set interfaces si-0/0/0 unit 2 family inet
set interfaces si-0/0/0 unit 2 service-domain outside
# create ipsec service-set for neo4
set services service-set ipsec next-hop-service inside-service-interface si-0/0/0.1
set services service-set ipsec next-hop-service outside-service-interface si-0/0/0.2
set services service-set ipsec ipsec-vpn-options local-gateway 172.20.13.1
set services service-set ipsec ipsec-vpn-options no-anti-replay
set services service-set ipsec ipsec-vpn-rules neo4
# create ipsec service rules for neo4
set services ipsec-vpn rule neo4 term 1 from destination-address 192.168.168.0/24
set services ipsec-vpn rule neo4 term 1 from ipsec-inside-interface si-0/0/0.1
set services ipsec-vpn rule neo4 term 1 then remote-gateway 172.20.13.20
set services ipsec-vpn rule neo4 term 1 then dynamic ike-policy ike-pol
set services ipsec-vpn rule neo4 term 1 then dynamic ipsec-policy ipsec-pol
set services ipsec-vpn rule neo4 match-direction input
# add static route to neo4 remote network
set routing-options static route 192.168.168.0/24 next-hop si-0/0/0.1
Strongswan (NEO4) ipsec tunnel to acx1100
NEO4 Podman network, container, and iptables rule related to Podman NAT and IPsec policy.
This is only informative configuration, details are out of scope here.
# create podman network
podman network create --subnet 192.168.168.0/24 --gateway 192.168.168.254 acx
# create podman container
podman run --cgroup-manager cgroupfs --rm -it --privileged --network=acx --ip=192.168.168.10 jonlabelle/network-tools
# iptables/ipsec policy for podman network
iptables -t nat -I POSTROUTING -s 192.168.168.0/24 -m policy --dir out --pol ipsec -j ACCEPT
Strongswan configuration
/etc/swanctl/conf.d/acx1100.conf
connections {
acx1100 {
version = 2
local_addrs = 172.20.13.20
remote_addrs = 172.20.13.1
proposals = aes128-sha1-modp1024
local {
auth = psk
id = "172.20.13.20"
}
remote {
id = "172.20.13.1"
auth = psk
}
children {
local-remote {
local_ts = 192.168.168.0/24
remote_ts = 10.0.0.0/30
esp_proposals = aes128-sha1
mode = tunnel
start_action = trap
}
}
}
}
secrets {
ike-acx1100 {
secret = "1q2w3e"
id-1 = "172.20.13.20"
id-2 = "172.20.13.1"
}
}
Validation
# load all swanctl configurations
root@noe4:~# swanctl -q
# list loaded configurations
root@noe4:~# swanctl -L
# list currently active IKE_SAs
root@noe4:~# swanctl -l
# ping from podman container
[network-tools]$ ping -c 3 10.0.0.2
# check acx1100 IKE SA
root@acx1100> show services ipsec-vpn ike security-associations 172.20.13.20 brief
# check detailed SA information
root@acx1100> show services ipsec-vpn ike security-associations 172.20.13.20 detail
# check acx1100 IPsec SA
root@acx1100> show services ipsec-vpn ipsec security-associations ipsec detail
# LRC ping NEO4 podman container
lrc@acx1100:lrc> show interfaces terse | match ge-0/1/1
lrc@acx1100:lrc> ping count 3 192.168.168.10
Wireshark - network switch between acx1100 and NEO4
NEO4 (podman container) → acx1100 (LRC):
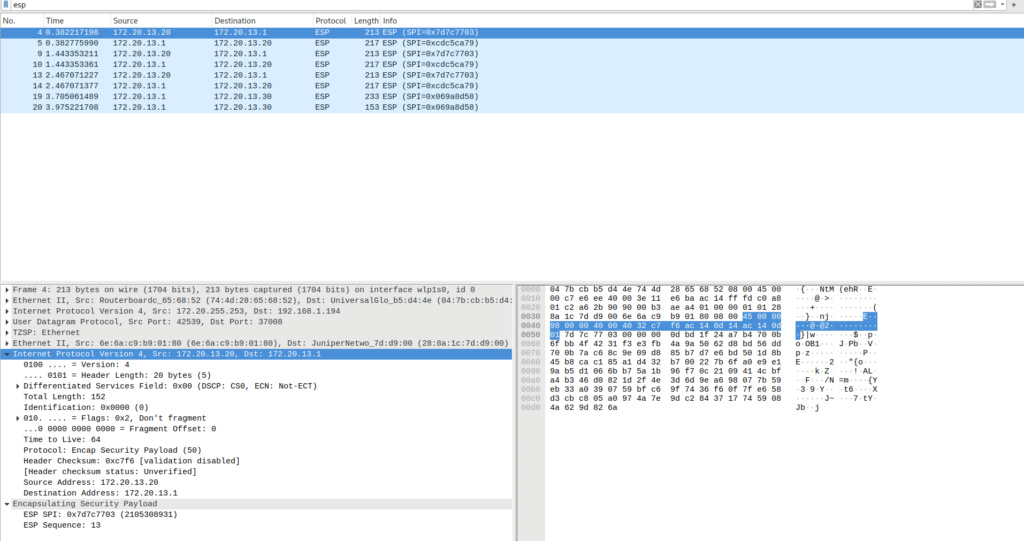
acx1100 (LRC) → NEO4 (podman container):
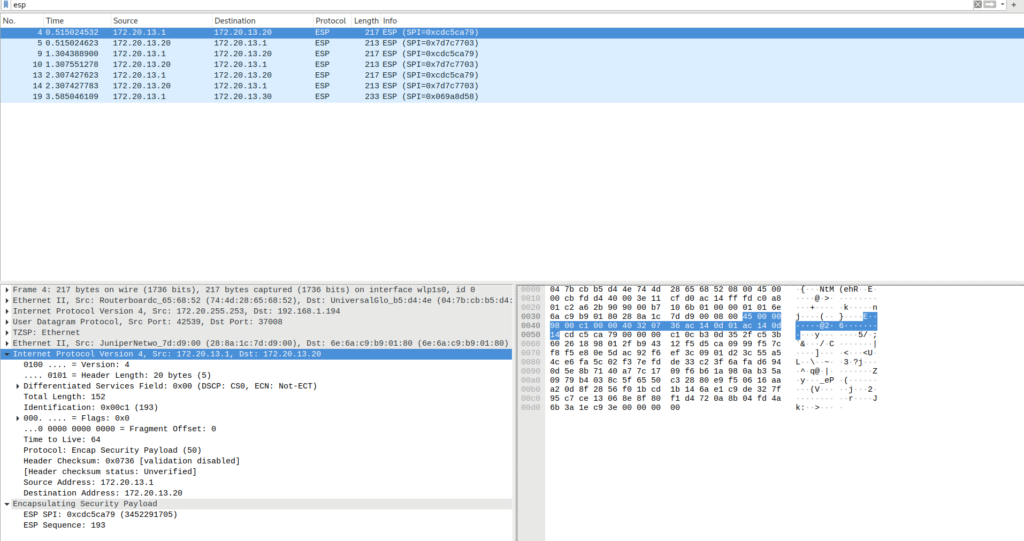
Final check – you should not see any unencrypted ICMP: